With the awareness of cyber threats, most companies spend a great deal of time on security controls. They aim to minimize the risks of cyber-attacks and invest in technology to implement good policy. The policies and technical solutions ‘we’ use, so the common reasoning – tend to conform to standards and products or services provided by reputable vendors. This gives ‘us’ confidence. ‘We’ are protected by being part of the crowd. And if it’s good for ‘them’ it’s good for ‘us’ as well. Yes, there is nothing inherently wrong with this approach. Yes, it is a solid strategy which will lead to meaningful results.
However, there is a weakness in this strategy and that is where we’re shining our spotlight today. Because what you DON’T see is what you miss.
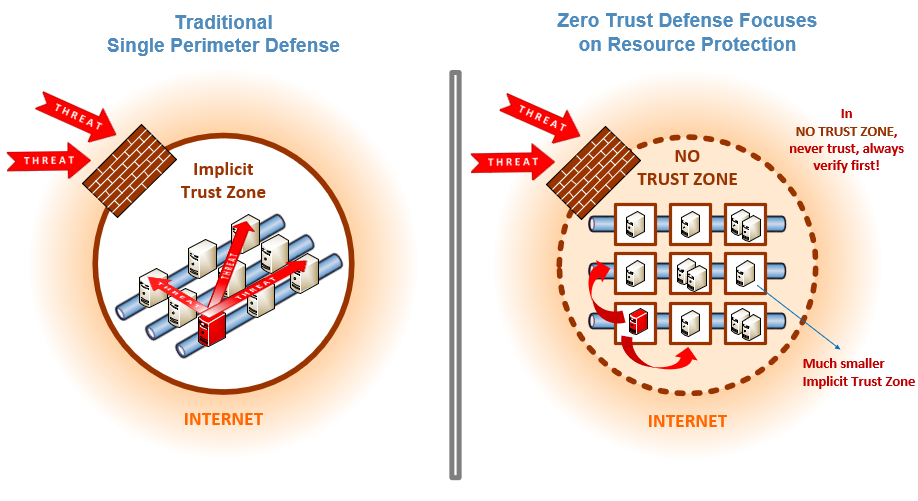
Illustration of the difference between a traditional, firewalled network, which is vulnerable to East-West traffic and a network with zero-trust architecture.
Credit: A. Kerman/NIST
The traditional and well-trodden route to most organizations’ goals is based on some rather naive assumptions. Adding a technical system to prevent threats is seen as reassurance that the problem has been addressed. When we look at the evolution of cybercrime, we saw people hacking applications to help developers improve resilience and protect systems from loss of data. While some developers respond well to this information, others simply chose to ignore or cover up their faults. At this stage, exploits and threats emerged to call out the poor responders and cybersecurity became a thing. Our defensive strategies are largely still routed in this thesis and, thanks to common standards and security systems available today, applications are no longer easy to hack by code exploitation.
However, cybercrime has evolved to be far more sophisticated today. When analysing the evolution of security breaches more closely, it becomes clear that direct attacks on applications are far less frequent. Every now and again, we read about a breach where a company leaves a database exposed on a public IP address with a default admin user config, but this is the exception.
Nowadays, we see more complex, multi–part approaches that progress through an organization. But for these cyber-attacks to succeed, there have to be a number of unattended, smaller “holes” in the organization’s defences. Often these exist as a consequence of flawed thinking that they have everything under control, but not properly checking because they thought they had it covered.
Most organizations are of course indirectly aware of other risks to their traditional security control investment. Hence the trend to steadily outsource non-core activity to “service providers”. Also the trend to use commodity infrastructure from Cloud providers to build and run new applications on. As a result, investment managers need to audit and align their security controls with those of the cloud provider.
Zero Trust and Shared Responsibility models are being incorporated into internal security control architecture to help firms adjust. But we still must cast a second pair of eyes on the landscape to understand where the cybercriminal may attempt his or her exploit in this situation. This a source of future “holes”, and we have noticed that many companies are taking too long to understand how their existing strategies fail to cover them.
Credit: A. Kerman/NIST
Just to round off the problem, let’s not forget the malicious or compromised employee who finds themselves inextricably linked to 90% of security breaches. Most of an organization’s investment still goes into external protection and detection but, employees people are often still in a position of trust and have access to information and systems. Are they being overlooked? Has the vulnerability they pose been considered? While we notice a higher awareness and more internal testing aimed at educating and protecting, we’d like to caution that this is not enough. The dark web is full of things about people and systems that most of us don’t know about.
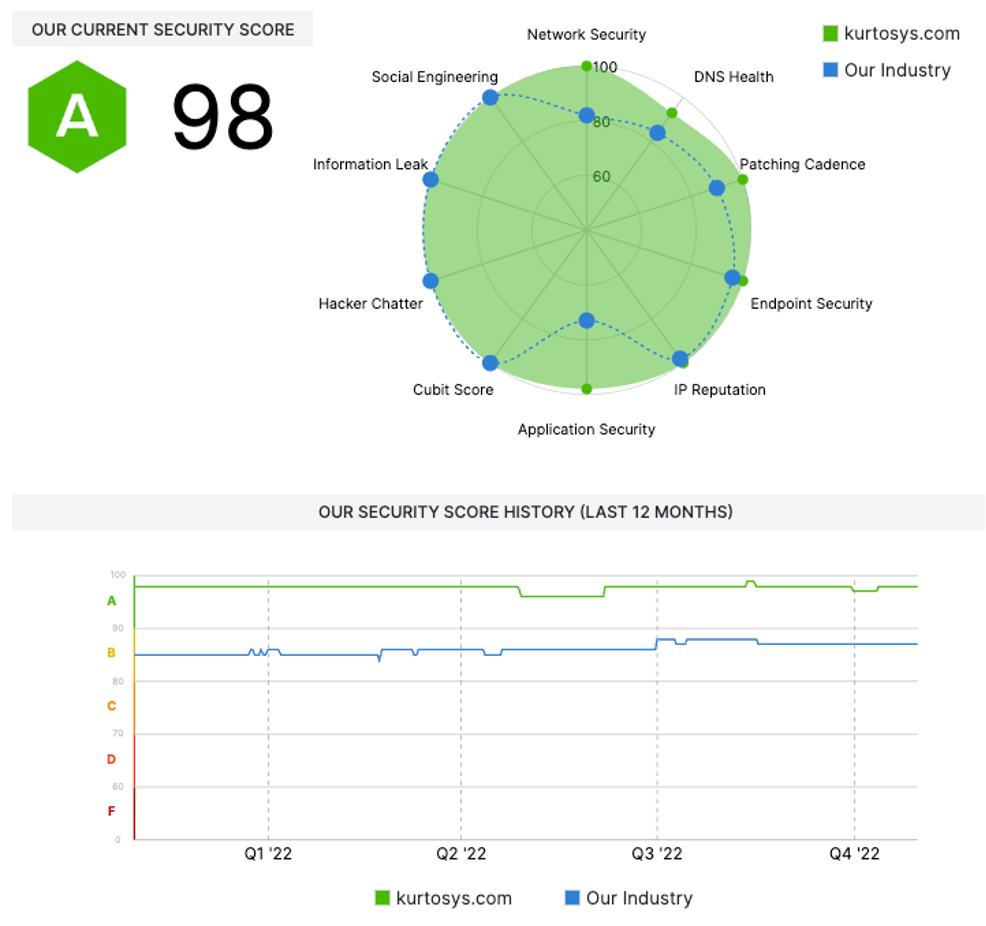
So how can you be sure that all the security controls that your organization has chosen are working correctly and providing adequate levels of protection? How can you see the things that are being missed or perhaps overlooked due to a false confidence in standards and technologies? One approach that we adopted here at Kurtosys is to use IT Vendor Risk Management (VRM) Tools ourselves to allow us to get ahead of the game. In turn, some of our Kurtosys clients have also started to use these tools to evaluate our services. To be specific, we chose to use Security Scorecard as we liked their down–to–earth and comprehensive ratings.
These tools provide us with just the insights we need. They confirmed our better–than–average security posture on day one. But, perhaps more importantly, presented us with a roadmap for improvement which helped us develop our way of checking and monitoring our effectiveness. We found many small but significant “holes” which we had overlooked. The VRM and vulnerability scanning tools continuously keep us focused on the impact of emerging threats and threat intelligence.
Security Scorecard uses 10 different measures to provide an overall evaluation of a company’s security posture. We probably only covered half of that with our standards and technologies in days gone by. Now we have a more robust picture. On the one hand, we use the tool in a conventional way to assess our key vendors and understand the downstream risks and focus our conversations with our partners. But it doesn’t stop there, because we also know that the threat can emerge from upstream in the supply chain. Hence we also use VRM to assess our clients’ weaknesses.
In conclusion, the key takeaway is to recognize that the traditional approach to security is a good start, but it can often mask the real threats. You have to stay alert and keep looking where you least expect a threat to appear. Embrace a mindset that allows your organization to continuously refine and improve its cybersecurity approach all the time.
References:
- World Economic Forum finds that 95% of cybersecurity incidents occur due to human error – cybernews.com
How Likely Is Your Employee To Cause A Data Breach? – forbes.com
How Cloudflare Security does Zero Trust – blog.cloudflare.com
Back to the future: What the Jericho Forum taught us about modern security – microsoft.com
The Key to Risk Intelligence: Visibility – securityscorecard.com