Data breaches are dangerous and costly – but this case study from South Africa can help us learn about prevention and forensic recovery.
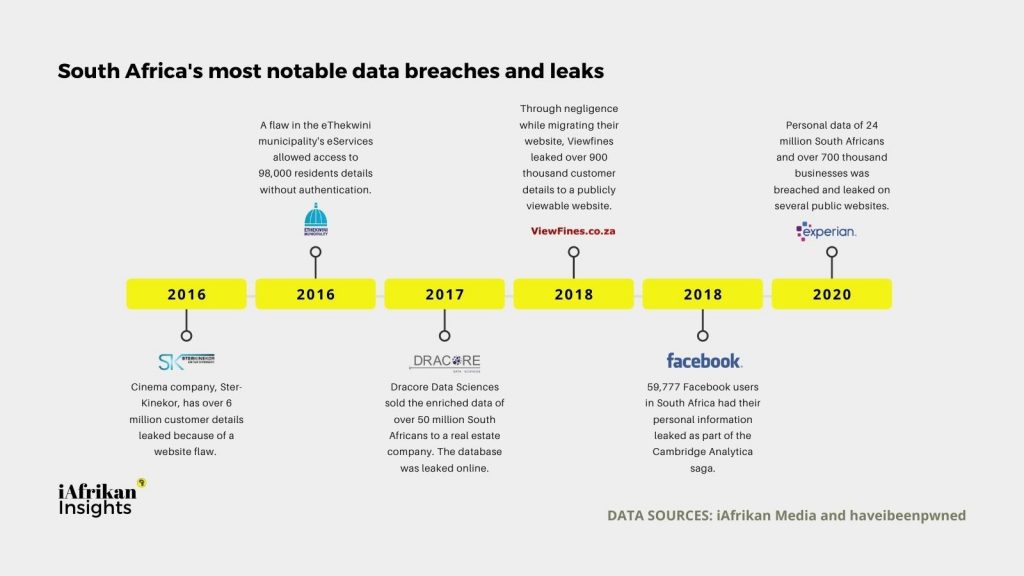
South Africa experienced almost 10 million malware attacks and a staggering 43 million potentially unwanted applications (PUA) in the first seven months of 2020, according to Kaspersky Security Solutions. The average security breach in the country cost companies R40.2 million ($2.7 million).
The three biggest causes of data breach in South Africa are malicious or criminal attack (48%), human error (26%) and system glitches (26%).
In the age of data, companies and individuals need to prioritize information security. Data is the new gold – it is highly valuable and easily found. But, it has also become increasingly easy for criminals to fool companies into handing sensitive data over to them, even more so during the pandemic. A company that fell victim to this type of fraud was Experian SA.

Image: www.cybersafe.news
Experian data breach insights
Experian SA is a data gathering and analytics company. Its products and services range from credit analytics to cybercrime and fraud analytics.
A scammer claiming to be a director of a well-known company committed fraud against the company. According to Experian SA’s CEO, the scammer provided “25 million names and identity numbers” of South African members of the public, which Experian verified. The scammer also provided data for around 790,000 businesses.
The scammer persuaded Experian to share data relating to these individuals and companies, including company registration details; general business information; company contact and credit profile information. For nearly 25,000 business entities, it also shared bank account numbers with the scammer.
Investigation and charges
Experian investigated the breach, identified the scammer, and opened a criminal investigation through an Anton Piller Order – a civil search warrant that replaces normal record discovery rules.
Such orders enable the applicant to search the defendant’s premises, without notice, and take possession of their records. Ordinary people can also use this warrant if they have evidence for a valid accusation. By having a Piller order approved by law enforcers, the company was able to find and impound the device the scammer used to commit the crime.
They did this by tracking the IP address used to send emails to Experian.
How forensics work
Further computer forensics in this case would also be able to locate and delete the stolen information.
Computer forensics apply investigative and analytical techniques for gathering and preserving evidence from a computing device. They aim to document the evidence’s chain of custody and create an analysis for presentation in a law court. The computer forensic process encompasses five stages as follows.

Image: www.businesstech.co.za
Identification
The first stage is to identify the purpose of the investigation and acquire the resources to conduct it. Experian would aim to find out what the crime was, how it was committed, where, when and by whom.
Resources allocated to this type of crime include personnel, such as computer forensic investigators and computer forensic analysts; and equipment for preservation, such as digital evidence bags, and a camera to record onsite evidence.
More resources would include hardware, such as SATA forensic disk controllers to extract data from the criminal device to be stored on a hard drive for further analysis; and software for computer forensic analysis, including Autopsy, Forensic Toolkit, Encase, and Windows Registry. Finally, the forensic team would also need a secure lab where they can conduct their investigations.

Image: www.portswigger.ne
Preservation
The next stage is isolating the data from the scammer’s device for preservation and analysis. The laptop used to commit the crime would have been retrieved in either a ‘live’ or ‘dead’ state. This means its hard drive was still running (live) or it was turned off (dead).
Investigators would take a picture of the crime scene to show the laptop was retrieved and document where and when. Pictures could have numbers assigned to them to help track what was taken from the scene.
The laptop would then be placed in a digital evidence bag designed to block any networks from accessing or altering data stored on it.
Retrieval
A SATA device would connect directly to the laptop, read and copy the data on its hard drive and essentially ‘paste’ the data onto an attached hard drive for forensic purposes.
This process ensures that the device remains intact and the data stored on it is not altered or deleted. Experian would likely not have deleted the data from the scammer’s laptop until after the case was completed.
Analysis
The extracted data would then be copied onto another laptop for forensic investigation and analysis.
Tools used in this stage of the process include Encase, which makes an ‘image’ copy of the hard drive. Another is Autopsy, which forensic teams use to locate and identify data that can be used as digital evidence in a case. Autopsy also has a reporting feature to gather the digital evidence and display it in a timeline of events for presentation purposes.
Documentation and presentation
The team would also document the chain of custody, which shows who has handled the evidence and to what point in the investigation.
Findings from the analysis phase are then documented for presentation. Experian and its investigators would then present their case, with support from the forensic process, in a court of law.
How to prevent cyber fraud
One lesson from cases such as Experian is that hackers are still willing to target individuals – including company employees or their clients – and can easily fool you into handing over valuable data. We are all human and make mistakes. Preparation and prevention are better than cure.
To aid prevention, be sure to learn from others’ mistakes, or from your own, and be more conscious of them.
Read up on the social engineering techniques that fraudsters use. Listen to your company’s security teams and read up on your company’s security measures.
Do your part in preventing such breaches by testing your knowledge on phishing emails and similar cyberattacks. Remember, criminals are just as human as we are, so it is crucial to stay one step ahead of them.

References
www.digitalguardian.com/blog/data-security-experts-reveal-biggest-mistakes-companies-make-data-information-security
www.experian.co.za/fraudulent-data-incident/faqs
www.guru99.com/digital-forensics.html#4
www.searchsecurity.techtarget.com/definition/computer-forensics
www.iol.co.za/business-report/companies/data-breach-costs-sa-companies-r402-million-average-in-2020-6649ae0a-b803-482c-978f- b395517c7fa7
www.iafrikan.com/2020/10/27/south-africa-biggest-top-data-breaches-leaks/