At Kurtosys we pride ourselves on information security, protecting our customer’s digital estates and ensuring we capture the most detailed data possible on the type of traffic that hits their websites. This gives our customer’s risk assessment teams critical information that support their threat detection mechanisms. My responsibilities at Kurtosys include helping our clients have consistent access to this type of information through our ISOC (Information Security Operations Centre) service.
Gerhard Vana – Information Security Engineer
Many asset manager websites have https configurations with an inadequate rating, potentially damaging their user experience and SEO ranking. 30% have below an A rating on Qualys SSL Labs, indicating significant secure protocol issues. Significantly more have at least one misconfiguration, according to analysis by Kurtosys.
Providing content over the secure protocol https can give your site a small advantage in search engine optimisation (SEO) compared to non-https pages. But an incorrectly configured https can do far more harm to your site than just damaging your SEO ranking. It can cause website outages, and damage user experience and your company’s reputation severely.
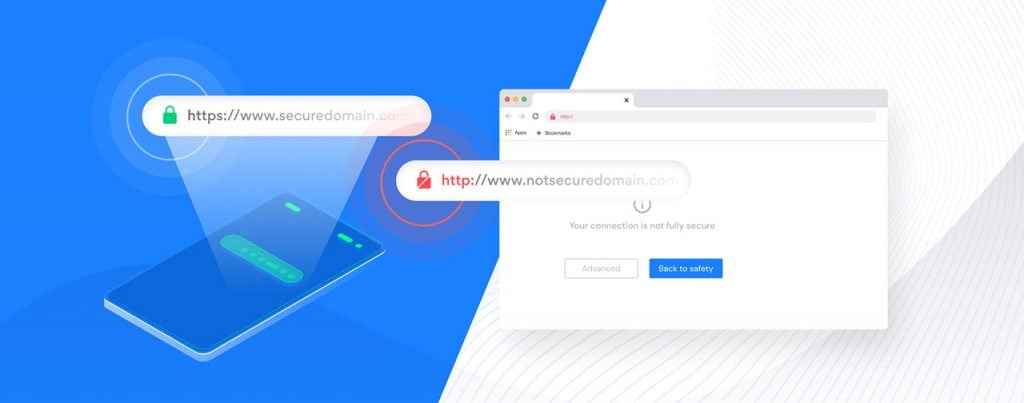
It starts with the browser
Hypertext transfer protocol secure (https) uses secure socket layer (SSL) and transport layer security (TLS) protocols to enable users to access websites more safely.
Browser developers are becoming far stricter in checking for certificates and certificate configurations that use outdated versions of these protocols. In July 2020, Google Chrome rolled out an update that prevented users from browsing sites using the older TLS1.0 or 1.1. The most recent version, released in 2018, is TLS 1.3. Microsoft, Safari and Mozilla soon rolled out similar updates to their browsers. This affected thousands of sites.
In Chrome’s version 86, released in October 2020, mixed content will not download unless an https equivalent is available. Other browsers react similarly, stating that the site is not secure, or refusing to connect.
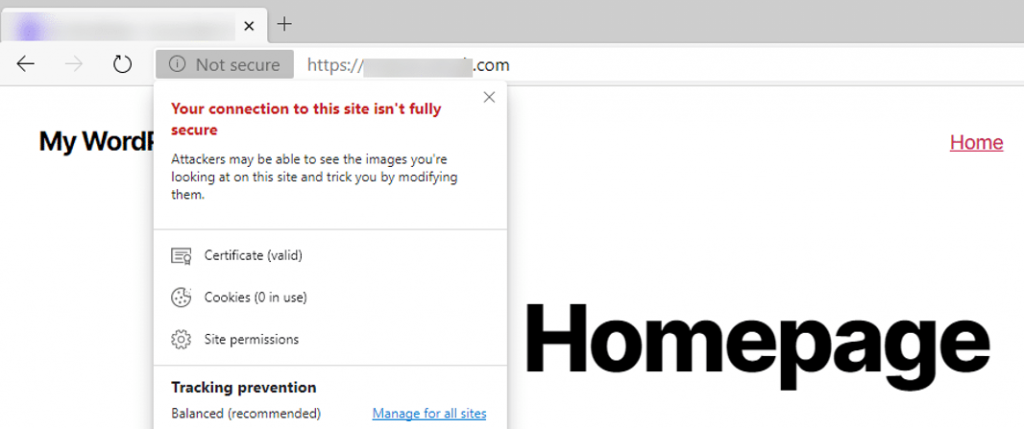
Here is an example of how Microsoft Edge would alert the user.
Here is how Chrome tends to do it.
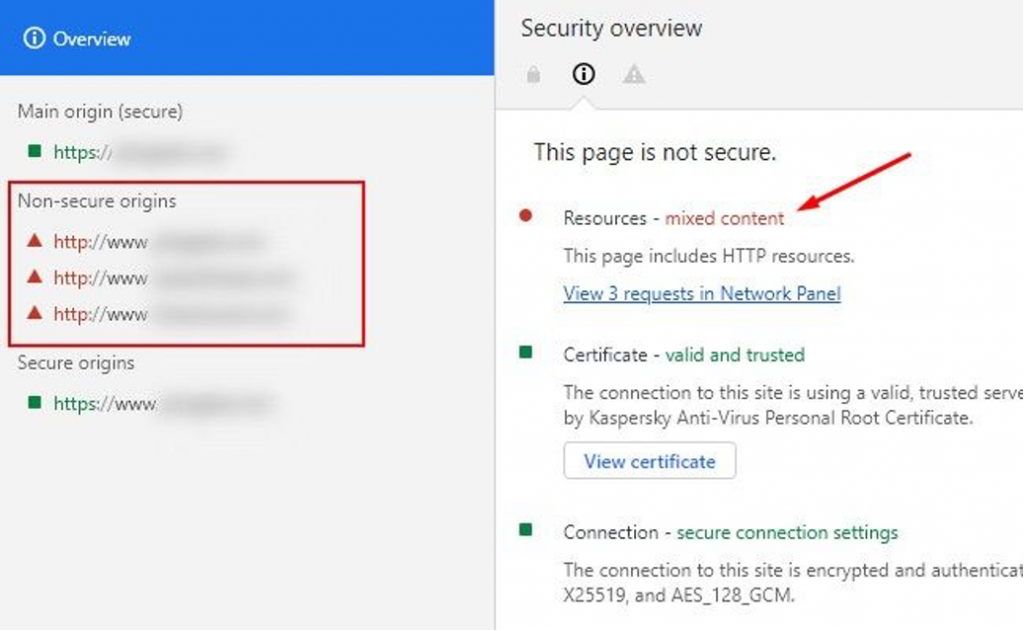
Neither look pretty and both would undermine user trust of your site. As browser developers add more checks around https, such errors will become commonplace unless we learn to avoid common misconfigurations.
Testing asset managers
How badly do these issues impact asset managers? To answer this, Kurtosys compiled a list of 30 asset management companies at random from the 2020 ADV Ratings top 50 asset management firms. We performed various checks on each of their website security using public data. Here are our findings, which should help you avoid nasty surprises when browser developers create extra checks.
Invalid certificates
Fortunately, we found only one (3.3%) of the 30 sites with a misconfigured or invalid certificate. The site’s main certificate has a valid expiry date, but the intermediary certificate has expired.
Of all the checks, this is the easiest to test and most important. Most browsers will warn the user, but some will refuse to connect to the site, so the impact will be significant.
Older TLS versions
My testing found 13 (43.3%) of the sites support old TLS versions. As mentioned, many browsers block TLS1.0 and 1.1, which date back as far as January 1999. Both suffer major security weaknesses and are significantly slower than later versions.
Fortunately, all the sites I assessed support later versions of the protocol and the server will usually try to connect using the latest TLS version.
But in some cases, where an error occurs with the handshake (server and client exchanging information required to establish a secure connection), the server could downgrade the connection. Should this happen, most up-to-date browsers will show an error message like this.
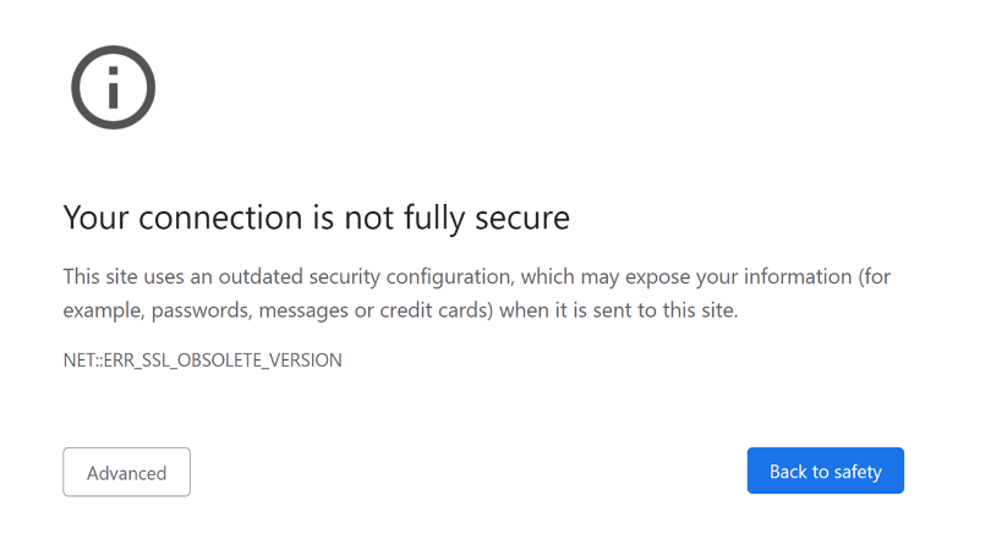
Again, this will impact user experience as the browser gives the user no option but to abandon the connection.
Configuration vulnerabilities
Of the 30 asset managers I tested, 11 (36.6%) have configuration-related vulnerabilities. One vulnerability common to all those 11 is secure, client-initiated SSL renegotiation.
When a user connects to a website using https, the client and the server attempt to negotiate a secure connection using TLS. If the server supports secure, client-initiated SSL renegotiation, an attacker could repeatedly request the server to renegotiate the connection.
The server needs additional resources to facilitate this. With enough requests, the server will eventually run out of resource and stop serving content.
The browser will not warn users of such vulnerabilities. But if exploited, there is a chance no users will be able to reach your site.
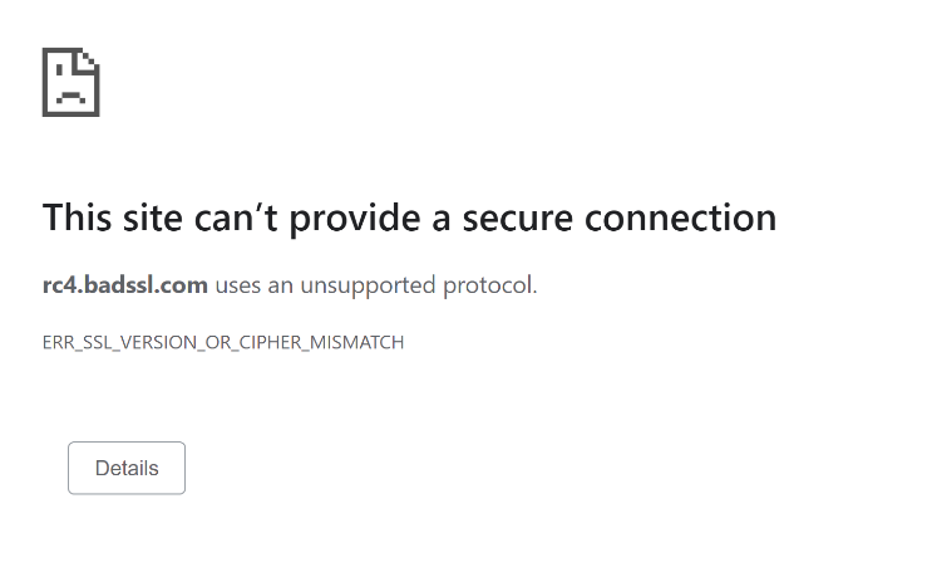
Weak ciphers
Of the sites I assessed, 16.6% support weak ciphers, which are algorithms used to negotiate security settings during the SSL/TLS handshake. This relates closely to sites that still support TLS1.0 and 1.1. Both versions support weak ciphers and browsers will warn users if they connect using any of the above protocols.
This is how Chrome might report a weak cipher.
Check your certificate rating
Many online services can help you check for the issues above. The industry standard is Qualys’ SSL Labs, which also rates your certificate on an alphabetical scale.
We used this as part of our analysis and found:
- 3% receive a T grade, which means the certificate cannot be rated due to critical misconfiguration.
- 6% rate as a B grade – supporting older TLS versions and not specifying preferred TLS versions on the server impact these sites the most.
- 3% get an A grade – minor configurations impact these sites, such as not emitting HSTS (http strict transport security) headers, which let browsers tell users they should only access them using https.
- 6% rate as A+, which means the certificate configuration has no major issues. This is what we should aim for.
Browsers do not check certificate ratings, but I encourage you to check them using SSL Labs. Anything below an A grade indicates there is something amiss with your site.
At Kurtosys, we do this as part of our go-live and maintenance procedures. If a certificate does not rate A or higher, we do not use it.



