At Kurtosys we pride ourselves on information security, protecting our customers’ digital estates and ensuring we capture the most detailed data possible on the type of traffic that hits their websites. This gives our customers’ risk assessment teams critical information that support their threat detection mechanisms. My responsibilities at Kurtosys include helping our clients have consistent access to this type of information through our ISOC (Information Security Operations Centre) service.
Gerhard Vana – Information Security Engineer
Financial services firms are 300 times more likely to be targeted by cyberattack than those in other sectors, according to a report by Boston Consulting Group. Yet most financial firms are ill-prepared for it.
The threats come from external and internal actors. This article focuses on external vulnerabilities, and my next article will cover internal threats.
According to IBM’s X-Force Threat Intelligence Report, the most common threat type in the financial sector is server access attacks. Our sector accounts for 36% of all these types of attack, which involve hackers accessing a company’s servers using stolen credentials, exploiting vulnerabilities, or other means such as social engineering.
The top attack vector is scanning and exploitation of vulnerabilities. Given that the US National Institute of Standards and Technology (NIST) filed 18,362 vulnerabilities in 2020 alone, identifying and mitigating them early is essential.

Annual penetration tests are dead. Long live penetration tests!
Most companies still rely on an annual penetration test to identify and fix vulnerabilities. But with 50 new vulnerabilities found each day, waiting a year to identify potentially critical issues is far too long.
At Kurtosys, we conduct an annual penetration test to confirm to our clients that our products are secure. But we also test all our client sites weekly. This allows for rapid identification of new vulnerabilities, after which we prioritize new bugs and hand them to our engineers for remediation.
We correct and mitigate any vulnerabilities we find as part of this process. Our software is updated regularly, so catching a potential issue before it hits production is essential. We have automated analysis tools that allow us to scan any new code for vulnerabilities before we deploy it. Plus, we run tools that check third-party libraries and plugins for known issues.
Websites are prone to regular external updates so, for these, we use continuous vulnerability scanning.

Not all threats are equal
The challenge with vulnerability and penetration tests is prioritization. What might look like a critical bug to an outsider might not be critical at all if adequate remediation is in place.
Let’s take two bugs as examples – secure shell (SSH) bypass attack, and WordPress cross-site request forgery (CSRF) vulnerability on contact forms.
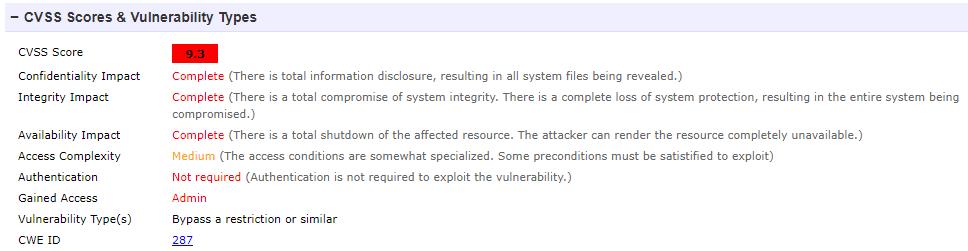
Fig. 1
Figure 1: secure shell (SSH) bypass attack
This allows remote attackers to bypass authentication via a crafted session and involves entry of blank passwords.
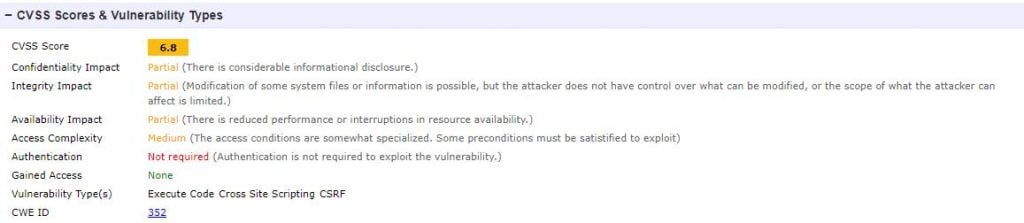
Fig. 2
Figure 2: WordPress cross-site request forgery (CSRF) vulnerability on contact forms
Before version 5.1.1, WordPress did not filter comment content properly. This led to remote code execution by unauthenticated users in a default configuration, leading to administrative access, which allows arbitrary changes to .php files.
On face value, the first bug appears the most critical. It allows an attacker to gain full control over your web server, whereas the second one would have a far lower impact.
But if these bugs existed on our stack, I would work on the second one first because I have inside knowledge of the stack. In this example, I know we block SSH to our systems, so the likelihood of exploitation is zero. An attacker would only be able to exploit the WordPress bug, so we would fix that first.
This is why it is important to combine test results with stack knowledge instead of blindly following priorities in a test report.

Getting the focus right
The OWASP top 10 list is an awareness document for developers and security experts, showing the most critical and exploited risks to web applications. We protect against all these ten attack types, which are:
- Injection attacks
- Broken authentication
- Sensitive data exposures
- XML external entities
- Broken access control
- Security misconfiguration
- Cross-site scripting (XSS)
- Insecure deserialization
- Using components with known vulnerabilities
- Insufficient logging and monitoring
But this is a different picture to what we see on our firewalls, where the top five attacks are:
- Distributed denial of service (DDoS) attacks
- Injection attacks
- XSS
- Broken access control
- Security misconfiguration.
If we simply followed the OWASP list, protecting against DDoS attacks would not seem that critical. But this is the most common attack on our stack. I am not saying that the OWASP list is incorrect, but a bit of local knowledge goes a long way. We must focus our efforts based on real-world data, not only generic lists.
Top tips for scanning and protecting your site
- Use annual penetration tests for assurance, not a primary driver for your security efforts.
- Test your site regularly, or ideally continuously.
- Prioritize based on actual risk, not perceived risk.
- Protect yourself against the top attack vectors based on a combination of best-practice and observed data.
At Kurtosys, we manage information security as part of our go-live and maintenance procedures.



