When outsourcing any solutions, there are always a number of factors to consider. We want to find a vendor that provides a solution which has a good match to our business needs. However, buyers will be reminded that this should be a fit of form and function. It may not be so obvious to the buyer how this can be achieved.
Vendors will sell based on the features and benefits that offer productivity and cost benefit, and this can obscure some of the other functions, or evaluation of functions, that are important in the selection processes.
This article will give you a clearer picture of how Information Security can help make and justify your outsourcing decision based on a model such as this.
Challenges with outsourcing
We are all familiar with the advantages of outsourcing such as:
- Leveraging the market-place for innovation and solutions
- Reducing in house, non-core costs and skills
- Contracted service and performance measures
However, there are some challenges to overcome. This is where a vendor with good Security posture will help and can demonstrate competence in areas such as:
- Websites and technology governance
- Performance of the service
- Operational control and management
A vendor who can demonstrate they have implemented an Information Security Management System to a standard such as ISO 27001 will be able to give you assurances regarding these challenges and reduce the concerns of other internal departments that need to ensure that vendors do not pose an undue risk.
Understanding the changes and mindset
Our IT, Network and Compliance departments have a default position to avoid and prevent data from leaving their sphere of influence and protection. We need to convince them that outsourcing is not a threat.
Vendors will use subcontractors to help provide their products and services. A good vendor will use Security to minimise the dependency and reliance on any given supplier.
Using a Security model to describe your outsourcing criteria
With any system selection, there is likely to be a Due Diligence process where your IT, Security and Compliance departments assess the. You can help focus their activity and shorten the evaluation by applying Information Security principles. This not only sets out important non-functional criteria, but it also describes these in ways that your colleagues can understand and do not need to challenge.
The diagram below shows how the use of CIA (Confidentiality, Integrity and Availability) can be used to categorise your organisations concerns.
Vendor should help you create these models and provide answers for their part. In fact, they should include this as part of the sales proposals.
You may also have to consider some of your own when it comes to the data you intend to use.
Creating a Risk Matrix to evaluate your vendor suitability
Risk Assessment is another commonly used method in Information Security to measure your Information Assets’ likelihood and impact rating against threats to the business. This can also be used to evaluate the position of each of your potential vendors.
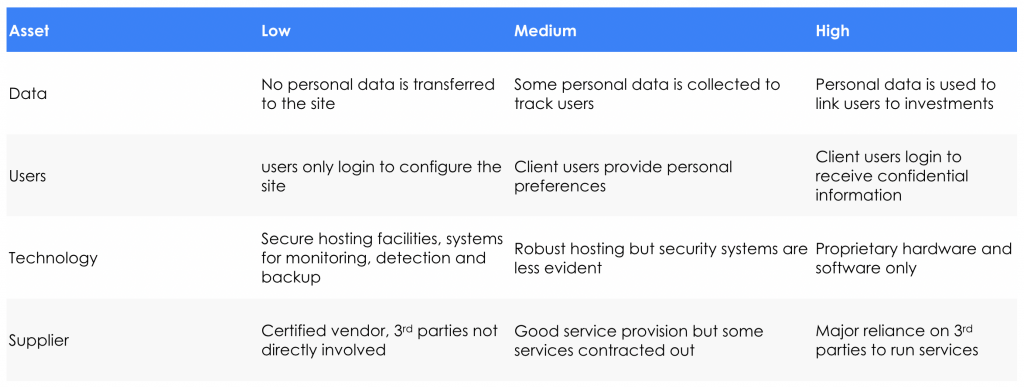
Each of your vendors will tick the boxes in one of the three columns: High, Medium or Low for each of the rows describing the asset types. This should provide a good qualitative risk assessment to indicate the vendors’ suitability.
Conclusions
As well as immersing yourself in the benefits and value that a vendor’s product has to offer, we have to remember that there are other factors that need to be addressed in order to have a successful outsourcing outcome. Information Security can help us get to that outcome quicker and lead to better long-term outcomes:
- Security builds a trust relationship between customer and vendor and develops a better understanding of issues that are important (or not) to each party
- Testing a vendor’s commitment and sincerity helps compare solutions and assess your options
- Asking and answering the right questions will reduce the risk profile of your solution and reduce the amount of Due Diligence you need to do
- Security methodologies will help develop recommendations that IT, Security and Compliance can sign off on



